Modern Identity Governance
and Administration
Omada’s IGA solution adapts to your organization
out of the box, while keeping you secure and compliant.

Omada’s IGA solution adapts to your organization
out of the box, while keeping you secure and compliant.
Omada was named Winner in the 20th Annual Globee® Awards for Cybersecurity in the cybersecurity solution and service category
This KuppingerCole Executive View report focuses on Omada Identity Cloud, an IdaaS offering provided by Omada, a leading IGA (Identity Governance & Administration) vendor.
"The Importance of Identity Governance Administration Solutions Within Modern IT Architectural Environments" highlights the changes in IGA and explains why it is now a mission critical program.
Why Omada
Omada provides the security, compliance, and efficiency required to remove cost
and uncertainty from managing identities and application entitlements
Complete transparency of identity and access risk helps to stop attacks on identity and prevent account breaches. Learn more
Achieve worry-free audits and regulatory compliance with comprehensive identity reporting you can trust. Learn more
Streamline business processes through optimized provisioning and seamless workflows that reduce helpdesk costs. Learn more
Omada Identity Cloud is based on over 20 years of experience and delivery of rapid and reliable identity results that give organizations the maximum value for their identity governance investment.
Our Products
Whether on-premise, hybrid or cloud, Omada can secure your workforce and machine identities
Omada Identity Cloud is an enterprise-grade, complete IGA Software-as-a-Service solution providing a full set of identity governance and access management functionality.
Omada Identity is a flexible and feature-rich IGA solution that delivers configurable identity and access management processes with essential identity governance and access management capabilities.
Our Differentiators
Analytics that improves decision-making, decreasing manual efforts to improve the TCO of your program
Automation of processes and workflows that can be configured without the need for code development
Compliance dashboard with drill-down actions and Control Policies that detect risks and enable remediation
Deliver operational IGA and a clear roadmap for maturity to get maximum ROI from your investment
Create, configure, upgrade, restore, and clone environments via an industry-leading management portal or via API
Omada Identity Cloud has the highest availability for the SaaS Identity Governance market
Standards-based framework leveraging SCIM, OData, REST, SOAP and SQL enables fast connectivity
The IdentityPROCESS+ framework provided out of the box to aid the delivery of a successful IGA deployment
TRUSTED BY LEADING ORGANIZATIONS GLOBALLY
"Omada is very user-friendly and at the same time a powerful tool that has so far answered 99% of our IAM needs!"
“Omada as a vendor is very supportive and capable, but most importantly - listening to their customers and…”
“Great IGA Software solution for the enterprise. Helps keeping your organization secure. Removes costs and…”
“Omada covers your full identity management lifecycle easily. The system really delivers on Omada’s promises.”
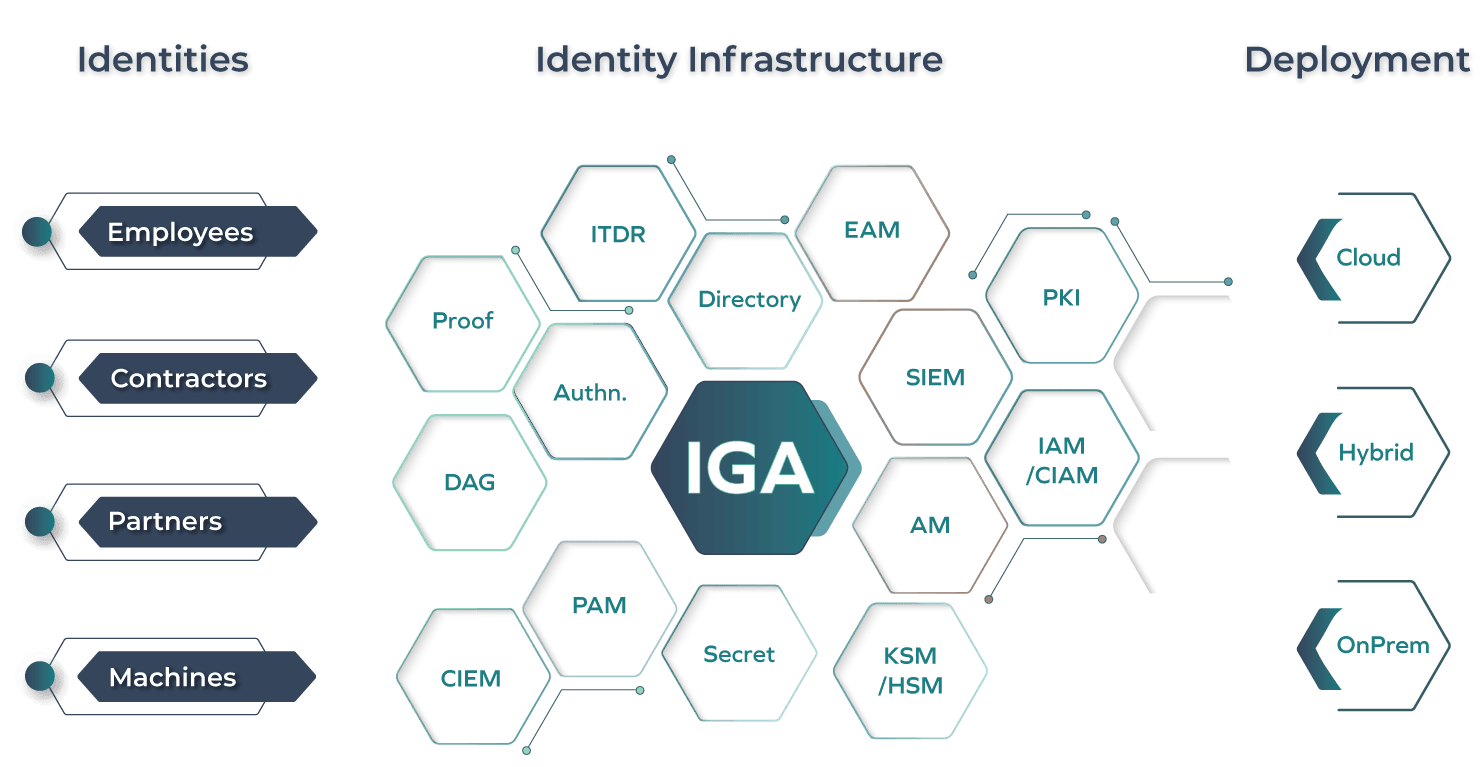
Omada Identity Cloud supports Identity Fabric infrastructure in four ways
As part of their digital transformation, DEKRA moved from an in-house developed access management solution to a modern, cloud-based Identity Governance and Administration (IGA) solution from Omada, which has led to significant productivity improvements, as well as substantial cost savings.
FEATURED RESOURCES
Join us for an exciting webinar that aims to guide you through the various technologies that enable the application of AI for IGA.
This report delivers reviews from end-users. Omada has one of the second highest "Willingness to Recommend" among vendors.
Join this webinar together with Omada’s Field Strategist, Paul Walker, who will walk you through the migration from a legacy identity system to modern IGA.
Let us show you how Omada can enable your business.