Overview
Improve Security, Achieve Compliance, and Maximize Efficiency with Modern IGA
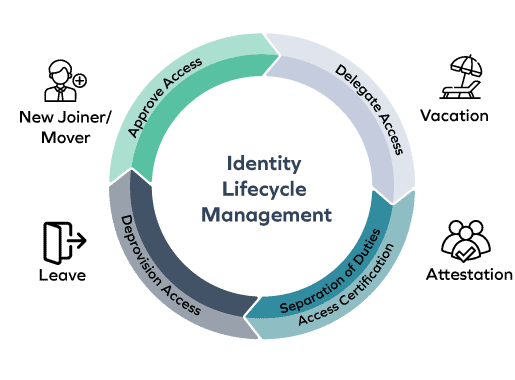
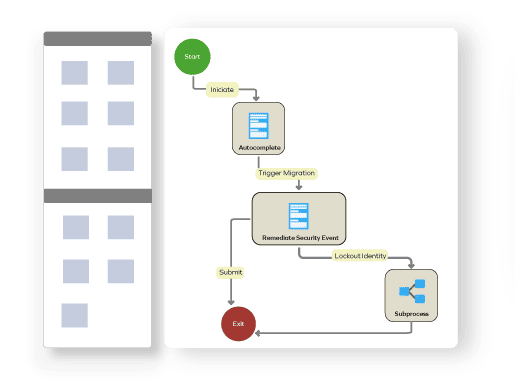
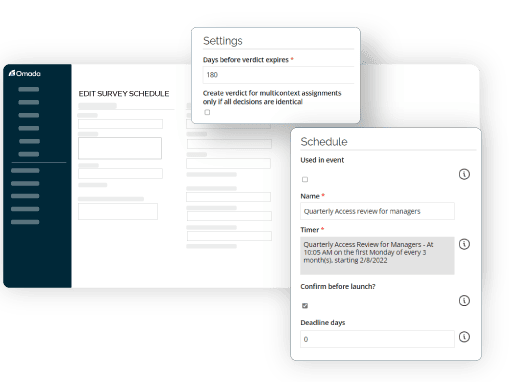
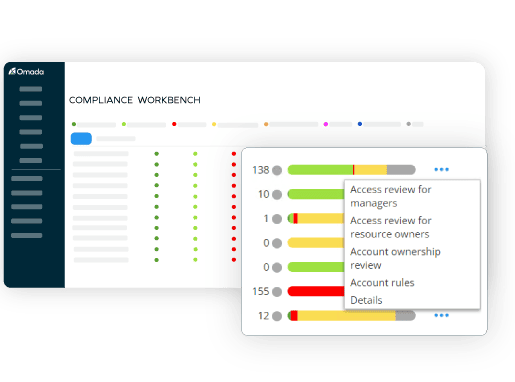
Omada Identity is a modern, enterprise-ready IGA solution that is deployed on-premises, giving you full control over your data and security. Our solution is easy to use, highly customizable, and gives you complete visibility into your environment without having to write a single line of code but is completely customizable to address any requirement. With built-in automation features, Omada Identity can help you streamline your workflows, improve efficiency, and strengthen your security posture.
Omada Identity mitigates security and compliance risks, optimizes efficiency, and secures digital identities for all users, applications, and data by providing a centralized platform for managing identities and access across all systems and applications. We help you define and decide who has access to what, when, and why.